Cloud Portal SCIM User Provisioning with Okta Identity Provider
Business Problem
Your organization is experiencing significant challenges in managing user identities and access permissions across the cloud applications. The manual processes currently in place are time-consuming, error-prone, and lacks the scalability needed to support your growing user base and expanding range of applications. To address these issues, you need to streamline and automate user provisioning and de-provisioning processes while ensuring robust security and compliance standards.
Requirements
- Access to an Infor CloudSuite
- User privileges for Infor Federated Service (IFS) User Management with the following roles:
- Optional Infor U courses:
- Infor OS: Identity and Access Management Fundamentals Workshop
Tutorial
Difficulty: Medium
Estimated completion time: 30 Minutes
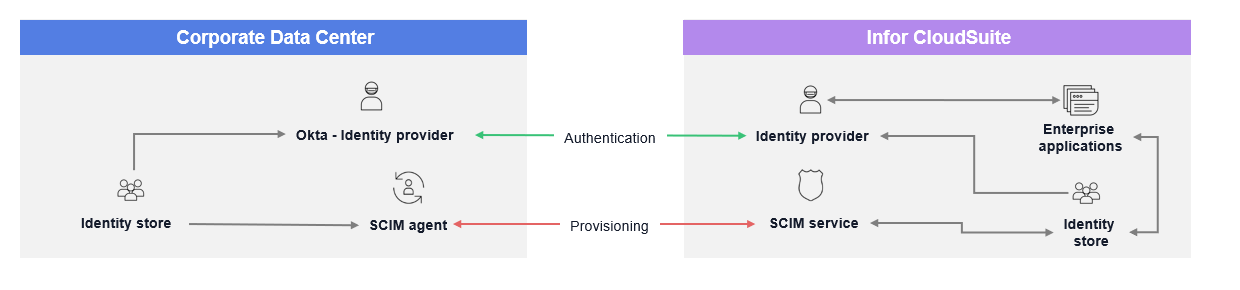
Implementing SCIM (System for Cross-domain Identity Management) user provisioning in the Infor Cloud Portal with Okta as the identity provider will automate the provisioning and de-provisioning of user accounts. This ensures seamless integration, as well as efficient and secure management of user identities.
Business Objective
- Automation and Efficiency:
- Reduce Manual Effort: Automate user account management processes to minimize manual intervention and associated errors.
- Accelerate Onboarding and Offboarding: Speed up the onboarding process for new employees and ensure timely de-provisioning of user accounts for departing employees.
- Improved Security and Compliance:
- Enhanced Access Control: Ensure that user access is consistently aligned with organizational policies and role-based access controls.
- Compliance and Auditability: Maintain comprehensive audit trails and compliance with industry regulations through automated provisioning and de-provisioning processes.
- Scalability:
- Support Organizational Growth: Provide a scalable identity management solution that can accommodate an increasing number of users and applications.
- Centralized Management: Simplify user identity and access management by centralizing it through Okta.
- User Experience:
- Consistent User Data: Ensure that user information is consistent across all applications and systems.
- Streamlined Processes: Improve overall user experience by reducing delays and errors in account provisioning.
This video provides instructions on how to configure Okta SCIM to automate the provisioning, deprovisioning, updating, and maintenance of user accounts in the cloud portal.
Familiarize yourself with the Infor Security Federation page and the Okta SCIM setup procedures.
By following the instructions in the video, you should now be able to set up the SCIM connection between the Cloud Portal and Okta Identity provider (IdP).
Resources
Help documents on configuring Okta SCIM with Infor CloudSuite.
For more information on identity provider federations and user provisioning setups, be sure to explore the Security and User Management with Infor Federation Services playlist.